How secure is my LinkedIn account ?
LinkedIn is a business-oriented Social networking service. One purpose of the sites is to allow registered users to maintain a list of contact details of people with whom they have some level of relationship, called Connections. Users can invite anyone (whether a site user or not) to become a connection. More details about LinkedIn can be found at http://en.wikipedia.org/wiki/LinkedIn
End of last year when I was checking my LinkedIn account I thought of giving a try to see how secure is my LinkedIn account. I noticed few very interesting but dangerous security issues.
Given below are few of the security issues I thought of sharing for learning purpose. Security issues mentioned below are only those, which have already got patched by LinkedIn recently.
Consider the following scenario:
Any valid LinkedIn user logs into his/her account and can Change/Add new Email address. Once user adds a new Email address, LinkedIn server sends a mail on the given (new) Email address with a message “Please confirm your email address”.
This looks like a normal process of adding a new Email Id. Isn’t it?
But there is an issue here,
LinkedIn does not force user or wait for user to confirm the newly added Email address and instead allows access to the LinkedIn account with the new Email address immediately.
An attacker can send a crafted link to the victim ( i.e. valid LinkedIn account holder) for adding an arbitrary Email address to his/her LinkedIn account. Attacker can send this crafted link on victim’s valid Email Id. Here attacker can try to use CSRF attack vulnerability.
For me it was not that simple to carry out CSRF attack, as it seemed that LinkedIn application was using adequate measures such as CSRF tokens.
After few analysis what was observed that if I know the server generated CSRF token of an authenticated session of victim then I can get this working and still carry out the attack on the victim.
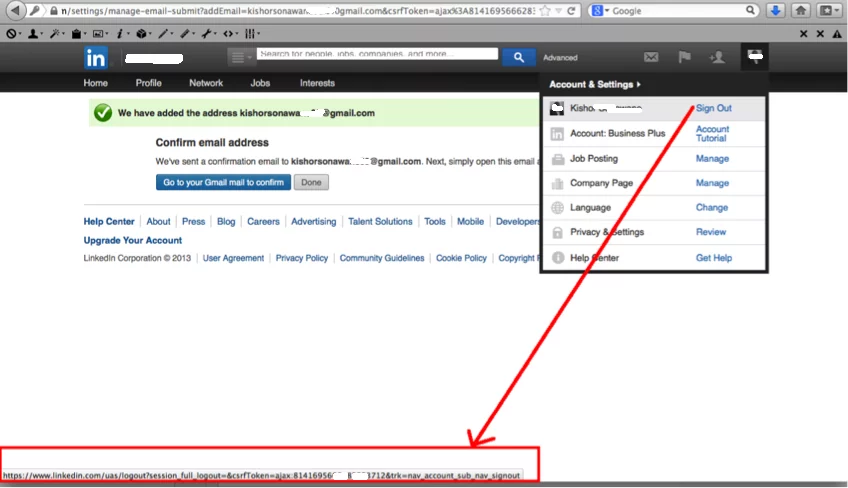
There is one trick to collect User’s CSRF token using Social Engineering technique, that is by asking victim user to show the Sign Out button, or some feature of LinkedIn etc. While she shows her logged in screens at that time quickly note down the CSRF token by either viewing the web page source or simply hovering the mouse pointer on Sign Out button as shown in the POC screenshot.
Figure 1: Application shows complete link with CSRF token on the Sign Out Button
Needless to say with Google Glass like technology where user can click photos on the fly will make this task very easy, as attacker just needs to view and take a snapshot of the screen showing the link with CSRF token, etc.
Let’s assume that attacker is successful in sending the crafted link to add a custom Email address on victim’s LinkedIn account. Attacker can achieve this either by the trick we talked above or finding actual CSRF vulnerability in the application. And that’s possible. In next blog I will discuss about how I found CSRF attack on LinkedIn.
Now let us continue understanding other important security issues,
The crafted CSRF link by attacker will be
https://www.linkedin.com /settings/manage-email-submit?a ddEmail=custom_email_id&csrfToken= ajax%3A0988969076258526585
On executing this link new Email address will get added into victim’s LinkedIn account without her knowledge. Let us see what happens then,
LinkedIn adds new Email address without any confirmation from the user.
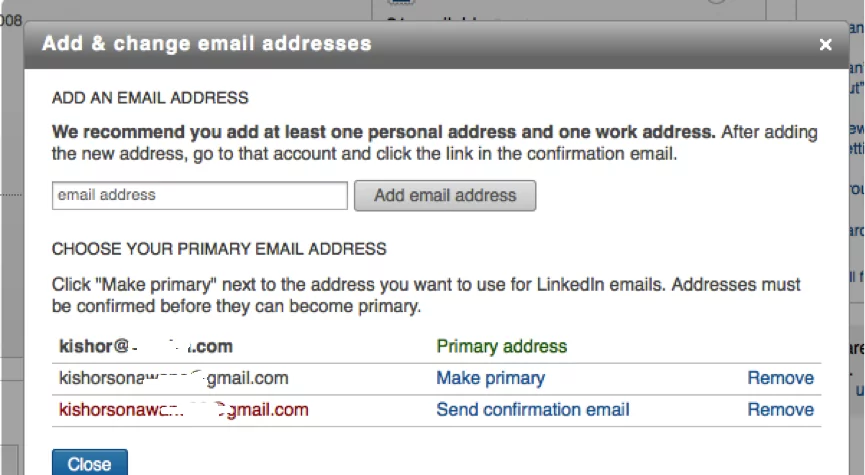
Figure 2: Application has added new Email address.
Lets ask a question here – After adding a custom Email address (in this case kishorsonawane08@nullgmail.com) by sending a crafted link to the victim, will LinkedIn still protect the victim by forcing him/her to first confirm the new Email address and then only activate it?
Ideally any secure application should confirm by the account holder whether she had added any new Email address. But that was not the case with LinkedIn.
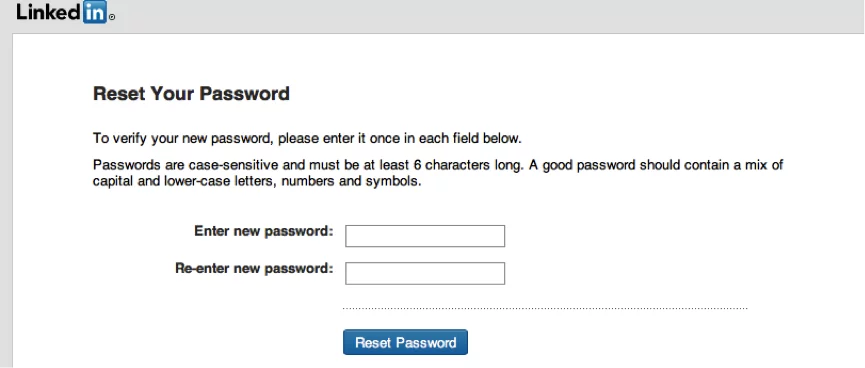
Without confirming the new Email address let us try to access the forgot password page and enters new Email address so that LinkedIn can send password reset token / code.

Figure 3: Accessing LinkedIn forgot password page
Shockingly, without confirming the newly added Email address, LinkedIn has sent the ‘Password RESET’ token on newly added Email Id. Bingo!!!
LinkedIn activates the new Email address without getting any confirmation from the user and sends password reset link .
As you must have observed that the password reset token was sent on newly added Email address meaning on attacker’s Email address.
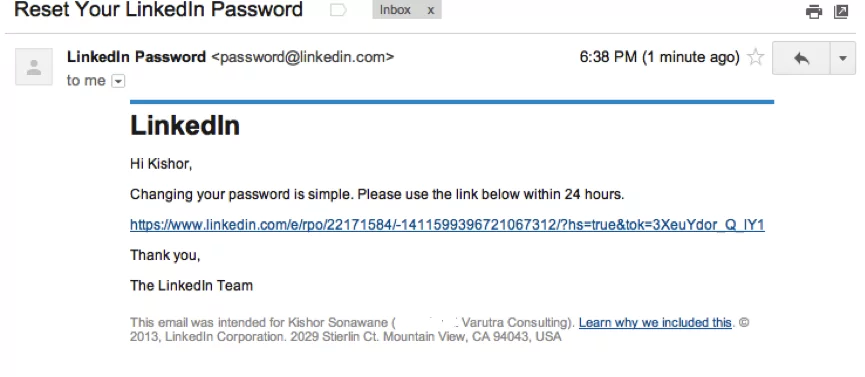 Figure 4: LinkedIn has sent a mail with password-reset token/link.
Figure 4: LinkedIn has sent a mail with password-reset token/link.
Figure 5: Attacker can set new password and also reset all other recovery options and compromise the account completely.
There was one more severe issue observed here.
User cannot remove arbitrary Email address from LinkedIn account, which was added by attacker.
If victim comes to know that he/she has not added the new Email address and wants to remove it then also he/she cannot do it. Isn’t it more shocking???
Application does not remove newly added Email address and force user/victim to first complete the confirmation by log in to the account.
Now the biggest question here is how can victim user will confirm this new Email address, which he/she has not added as well as has no access to that Email account also.
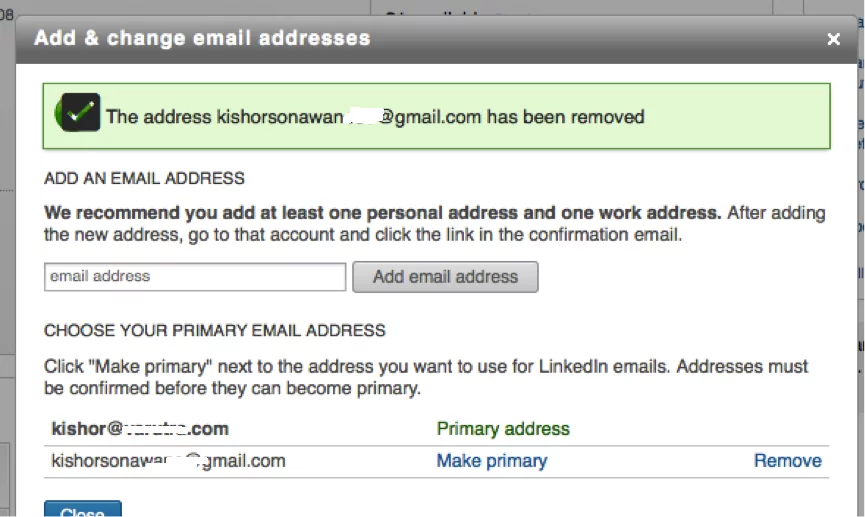
If user tries to remove this Email address from LinkedIn, application shows following message that the address has been removed but in reality IT WILL NOT. If user checks the email settings she will found that the Email address has not gone. So victim is helpless here.
Figure 6: Application shows that the newly added Email has gone but it does not remove it in reality.
Insecure Password Reset Module
LinkedIn enables the password-reset link for 24 hours. Ideally as a best practice, on clicking the password reset link and successfully resetting the password, the link should become inactive. But even after resetting the password this link will be valid for 24 hours, which is dangerous in case of the account is compromised, and attacker has the password-reset link on his Email address.
This means if user comes to know that his account might be compromised with other Email address and if he/she changes the password, still attacker can use the password-reset link to change the password again and take control of it.
When contacted LinkedIn they have accepted these issues and mitigated them. Few more issues are getting patched. Till then happy Social Networking.
Read it on packet storm
Written By,
Attack & PenTest Team,
Varutra Consulting